Implement SSO authentication
Single Sign-On (SSO) allows users to log in to PandaSuite using their corporate identity, without needing to create an additional account. PandaSuite supports both SAML v2 and OpenID Connect (OIDC), used by many identity providers (IdP) such as Azure AD, Google Workspace, Okta, Auth0, etc.
SSO can be enabled in two places:
- On the editor side → For users accessing PandaSuite Studio.
- On the web app side → For applications created with PandaSuite (Web App / PWA).
These two configurations are independent. You can enable SSO for Studio, for a web app, or both. For each area, you choose one protocol (SAML or OIDC).
What is SSO?
Single Sign-On (SSO) is an authentication method that allows users to securely log in to multiple applications with a single credential.
Why use SSO?
- Enhanced security: fewer passwords to manage, reducing the risk of phishing.
- Seamless experience: smooth login without repeated authentication.
- Centralized management: access controlled by the IT administrator via an IdP.
The SAML v2 protocol
SAML (Security Assertion Markup Language) is an XML standard that allows a service provider (SP), like PandaSuite, to delegate authentication to an identity provider (IdP).
The OpenID Connect (OIDC) protocol
OpenID Connect (OIDC) is a modern protocol built on OAuth 2.0. It allows a service provider (like PandaSuite) to delegate authentication to an identity provider and receive standardized identity information (claims).
How does SSO work?
SSO is based on a secure exchange of authentication tokens between PandaSuite and your identity provider (IdP).
- The user attempts to access PandaSuite or a web app.
- PandaSuite sends an authentication request to the IdP with a token containing the user’s email.
- The IdP checks if the user is already logged in:
- ✅ If yes, access is granted immediately.
- 🔄 Otherwise, they are redirected to their company’s login page.
- The user authenticates with their IdP (e.g., Microsoft 365, Google, Okta credentials, etc.).
- The IdP validates the identity and sends authentication information back to PandaSuite (SAML assertion or OIDC token).
- PandaSuite validates it and grants access to the user.
Everything happens in the background, without the user having to enter a password on PandaSuite!
Setting up SSO for a web app
Currently, SSO authentication is only compatible with web apps / PWA. For a native application, please contact our team.
-
Retrieve PandaSuite information
- Access your PandaSuite account
- Go to the Apps section and select your web app
- Go to the Security tab
- Enable SSO
- Select a Protocol (SAML or OIDC)
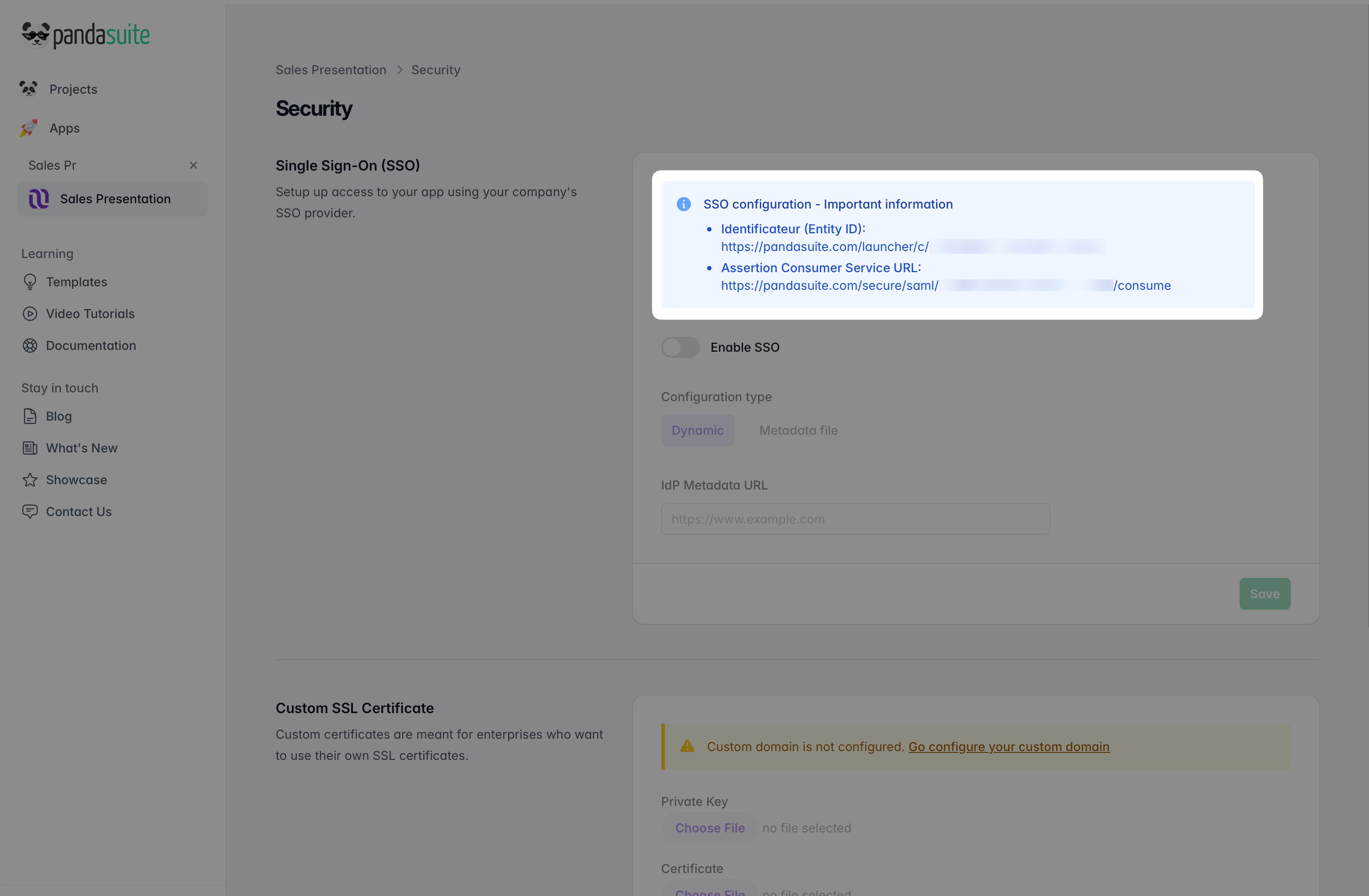
PandaSuite automatically provides you with the following information (depending on the selected protocol):
- SAML
- Entity ID:
https://pandasuite.com/launcher/c/[APP_ID] - Assertion Consumer Service URL:
https://pandasuite.com/secure/saml/[APP_ID]/consume
- Entity ID:
- OIDC
- Callback URL:
https://pandasuite.com/secure/oidc/callback
- Callback URL:
-
Configure your identity provider (IdP)
Use the information above to configure your PandaSuite application in your identity provider (Azure AD, Google Workspace, Okta, etc.).
-
Finalize the configuration in PandaSuite
- If you selected SAML:
- In Configuration type, choose Dynamic to paste the IdP Metadata URL, or choose Metadata file to upload your metadata file.
- If you selected OIDC:
- Fill in Issuer URL, Client ID, and Client Secret.
- If a client secret is already configured, leave Client Secret empty to keep it unchanged.
- Optional: adjust Scopes (default:
openid,email,profile) and User ID Claim (default:sub).
- Save the configuration and test the connection.
- If you selected SAML:
Optional: Restrict access with Access Rules
In the Security tab, you can create Access Rules to restrict access based on:
- SAML attributes (including the NameID field)
- OIDC claims (including the Subject (sub) claim)
Setting up SSO to access PandaSuite Studio
-
Request creation of your organization
- Contact the PandaSuite team to request the creation of your SSO organization
- Confirm which protocol you want to use (SAML or OIDC)
- The PandaSuite team will provide you with the necessary information (depending on the selected protocol):
- SAML: Entity ID and Assertion Consumer Service URL
- OIDC: Callback URL
-
Configure your identity provider (IdP)
Use the information provided by the PandaSuite team to configure PandaSuite Studio in your identity provider (Azure AD, Google Workspace, Okta, etc.).
-
Send IdP metadata
- If you selected SAML: send the PandaSuite team the XML metadata file from your identity provider or a metadata URL.
- If you selected OIDC: send the PandaSuite team the Issuer URL, Client ID, and Client Secret (and optional Scopes and Email Claim).
-
Finalization
Once the configuration is completed by the PandaSuite team, your users will be able to access PandaSuite Studio via SSO.